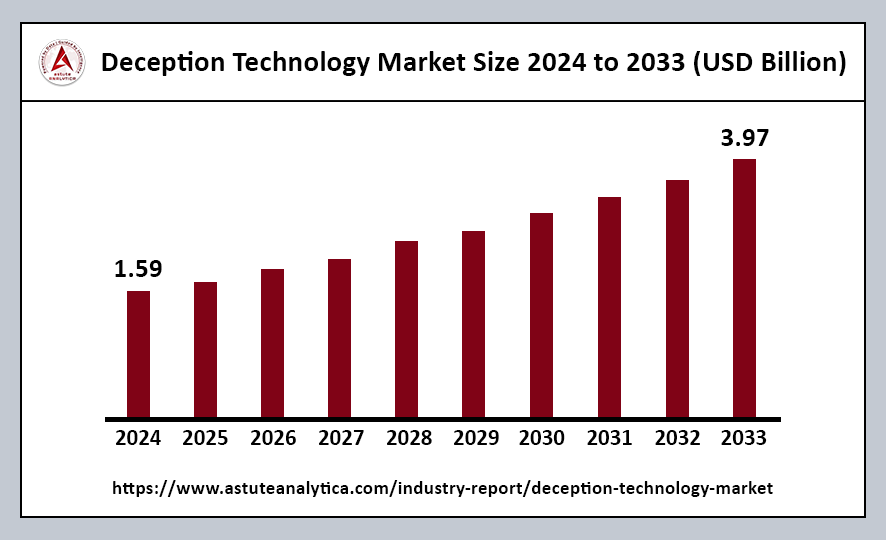
The global deception technology market was valued at US$ 1.59 billion in 2024 and is projected to reach US$ 3.97 billion by 2033, reflecting a Compound Annual Growth Rate (CAGR) of 11.45% during the forecast period from 2025 to 2033.
The Deception Technology market is experiencing rapid growth, fueled by the increasing frequency and sophistication of cyberattacks across various industries. As organizations become more vulnerable to advanced persistent threats, ransomware, and other forms of cybercrime, the demand for innovative cybersecurity measures is intensifying. In five major nations—including the United States, China, Japan, Russia, the United Kingdom, and India—twenty prominent banking groups have already invested in sophisticated honeypot deployments. Major sectors such as finance, defense, and healthcare are actively adopting these deception capabilities to entrap attackers and study emerging threats. By leveraging these technologies, organizations can enhance their security posture and proactively defend against the evolving landscape of cyber threats.
Deception Technology Market Key Takeaways
- By offerings, the solution segment currently holds over 65% of the deception technology market.
- In terms of end-use industry, the BFSI sector (Banking, Financial Services, and Insurance) occupies over 30% of the market share.
- Regarding deployment methods, cloud deployment accounts for more than 62% of the deception technology market share.
Regional Analysis
North America: A Hub for Deception Technology
North America, particularly the United States, has emerged as a hotspot for the deception technology market, driven by the increasing frequency and evolving sophistication of cyber-attacks. Currently, the region holds over 30% market share in this rapidly growing sector, reflecting the urgent need for advanced security solutions.
- Addressing Insider Threats: A notable trend in the U.S. is the heightened use of deception technology to enhance the detection and mitigation of insider threats. Organizations are becoming increasingly concerned about the potential for malicious actions by employees, contractors, or partners who have legitimate access to critical systems and data.
- Utilizing Deception Tools for Detection: To combat these insider threats, deception tools are employed to create decoy assets and environments. These decoys effectively lure and detect suspicious behavior within networks, allowing organizations to monitor interactions and identify potential risks before they escalate.
Rising Cyber Threats in Europe
The Europe region is confronting an increasing number of sophisticated cyber threats, which include ransomware, phishing, and insider attacks. As these threats become more complex and prevalent, organizations are compelled to enhance their security measures to safeguard their digital environments.
- Leveraging Deception Technology: To bolster defenses, deception technology is being employed to create decoy systems and data that effectively attract and identify malicious activities. By setting up these deceptive environments, organizations can lure potential attackers into engaging with decoys, allowing them to monitor and analyze interactions with these systems.
- Early Threat Detection and Risk Mitigation: Through the analysis of interactions with decoys, organizations can detect threats early and mitigate risks before they significantly impact critical operations. This proactive approach is vital in strengthening the cybersecurity posture of businesses across Europe, enabling them to respond swiftly to emerging threats.
- Protecting Critical Assets: Ultimately, the implementation of deception technology helps businesses protect their intellectual property, financial assets, and sensitive information from evolving cyber threats. By adopting this innovative strategy, organizations in Europe can better defend against the increasing complexity of cyber risks and maintain the integrity of their operations.
Rapid Growth of Cybersecurity in Asia Pacific
The Asia Pacific region is anticipated to register the fastest CAGR (Compound Annual Growth Rate) over the forecast period. This growth is attributed to the increasing prevalence of cyber threats and security concerns, which are being driven by rapid digital transformation and enhanced connectivity across the region.
- Adoption of Deception Technology: Organizations are utilizing deception technology to bolster their defenses against advanced cyber-attacks, including ransomware, phishing, and nation-state threats.
- Enhancing Cybersecurity Posture: A proactive approach to cybersecurity helps identify potential threats and provides valuable insight into attacker behavior. As organizations in the Asia Pacific region adopt these technologies, they strengthen their overall cybersecurity posture, enabling them to better protect critical data, intellectual property, and infrastructure from evolving threats.
Top Trends Escalating the Deception Technology Market
AI-Driven Decoy Platforms: AI-driven decoy platforms play a critical role in modern cybersecurity by continuously adjusting lures to intercept advanced threats effectively. This adaptability enhances the chances of detecting sophisticated attack methods and misdirecting potential intruders, making it increasingly challenging for them to accomplish their malicious objectives.
Hybrid Cloud Deception Strategies: Hybrid cloud deception strategies represent a significant advancement in cybersecurity, merging endpoint illusions with micro-segmentation layers. This innovative approach enables organizations to create complex security frameworks that isolate and deceive attackers effectively.
Enhancing Decoy-Based Forensics with Real-Time Threat Intelligence: Real-time threat intelligence feeds are essential for enhancing decoy-based forensics, particularly in the context of attacker profiling. This information is instrumental in refining decoy strategies, allowing for more effective profiling and a deeper understanding of the threat landscape.
Urgent Decoy-Driven Security Adoption Amid Insider Infiltration: The prevalence of explosive insider infiltration methods has amplified the urgent need for decoy-driven security adoption worldwide. Organizations are increasingly recognizing that insider threats can pose significant risks to their security posture. Decoy technologies offer an effective means of identifying and mitigating these threats before they lead to substantial damage.
Decoy Orchestration in Response to Rising Industrial Espionage: The rise in industrial espionage has fostered a trend toward decoy orchestration that extends beyond conventional threat defenses. As organizations face increasing competition and the targeting of intellectual property, sophisticated deception technologies are being employed to safeguard critical assets.
Demand for Proactive Attacker Engagement: The growing demand for proactive attacker engagement is driving the need for deception ecosystems across diverse digital environments. Organizations are beginning to understand that merely reacting to threats is no longer sufficient; a more interactive approach to cybersecurity is necessary.
Deception Technology Market Segmentation
By Offerings
Deception technology solutions in endpoint, data, and network security have matured into indispensable components of modern cybersecurity. These advanced systems have become essential for organizations looking to enhance security measures and proactively combat cyber threats. Today, organizations that implement these deception technology systems have significantly improved their threat detection capabilities, reducing their average time to detect threats by an impressive 91 hours compared to traditional security methods. This remarkable improvement underscores the effectiveness of deception technology in identifying and mitigating security risks more efficiently.
By End Use Industry
In the BFSI (Banking, Financial Services, and Insurance) sector, the deception technology market has emerged as a robust defense mechanism to combat the increasing complexity of cyber threats within financial ecosystems. As financial institutions face sophisticated and evolving attacks, the adoption of innovative security measures has become imperative.
Currently, nearly 1 in 3 BFSI companies are using or actively considering deception technology as a crucial component of their cybersecurity arsenal. This strategic approach has proven instrumental in preventing wire transfer fraud by creating convincing fake SWIFT environments that effectively mislead attackers. By implementing deception technology, these organizations can enhance their defenses and protect sensitive financial transactions from cyber criminals.
By Deployment
Cloud-based deception technology solutions have fundamentally redefined security implementation through their unmatched agility and efficiency. These advanced cloud-first deception platforms are designed to safeguard critical enterprise risks by protecting various aspects such as cloud workloads, endpoints, identities, and sensitive data. This strategic convergence of cloud infrastructure and deception technology is shaping a new standard in adaptive cyber defense. By leveraging the capabilities of the cloud, organizations can enhance their security posture, effectively countering evolving threats and ensuring robust protection for their digital assets.
Deception Technology Market Recent Developments
- Infopercept’s New MDR Solution: In March 2025, Infopercept announced its new MDR solution called ‘Real MDR Solution.’ Delivered through Infopercept’s consolidated cybersecurity platform ‘Invinsense,’ the solution offers comprehensive cybersecurity coverage beyond traditional MDR offerings.
- SEC’s New Cyber Unit: In February 2025, the U.S. Securities and Exchange Commission (SEC) unveiled a powerful new weapon in its fight against digital deception. The Cyber and Emerging Technologies Unit (CETU) will tackle rampant fraud in crypto.
- CloudSEK’s Deep Fake Detection Technology: In October 2024, CloudSEK announced the launch of its state-of-the-art Deep Fake Detection Technology, which is now available for free. This initiative is part of CloudSEK’s commitment to providing valuable resources to society and combating cybercrime.
Top Companies in the Deception Technology Market:
- Rapid7 Inc
- Attivo Networks
- Illusive Networks
- Guardicore
- Trap Data Security Ltd.
- Acalvio
- Cynet
- ForeScout
- Morphisec
- Zscaler
- Logrhythm, Inc.
- Topspin Security
- Other Prominent Players
Market Segmentation Overview:
By Offering
- Solutions
- Endpoint Security
- Data Security
- Network Security
- Services
- Professional Services
- Managed Services
By Deployment Mode
- On-Premises
- Cloud
By Enterprise Size
- SME’s
- Large Enterprises
By Industry
- BFSI
- Government and Defense
- Healthcare
- IT and Telecom
- Retail
- Energy and Utilities
- Manufacturing
- Others
By Geography
- North America
- Europe
- Asia-Pacific
- Latin America
- Middle East and Africa
Source: https://www.astuteanalytica.com/industry-report/deception-technology-market
















