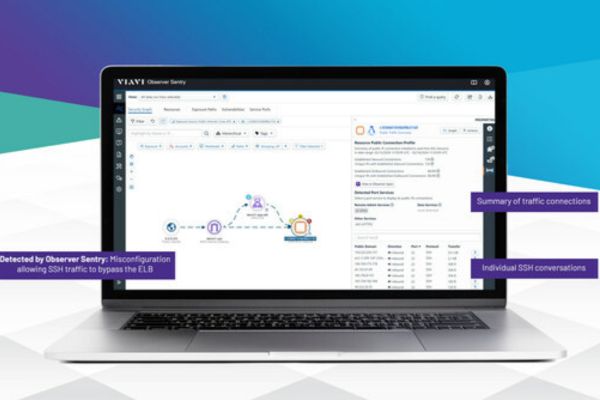
VIAVI Solutions announced the addition of traffic analysis capabilities to its Observer Sentry Software-as-a-Service-based threat exposure management solution. With traffic visibility, Observer Sentry goes beyond identifying unintended and potentially dangerous exposures, and enables SecOps, DevOps and cloud architects to determine if a vulnerability has been exploited.
Observer Sentry audits security groups, access control lists, firewall rules and other sources of configuration to identify resources and relationships across all AWS accounts. This analysis locates the misconfigurations and overly permissive settings that create unwanted exposures. Integration with vulnerability scanners allows Observer Sentry to automatically prioritize the remediation of critical vulnerabilities.
Traffic integration enhances Observer Sentry’s exposure and vulnerability analysis by comparing what the configuration will allow with visibility into actual events. In addition, integration with the VIAVI Observer Apex performance monitoring solution enables forensic-level traffic analysis if an exposed resource is compromised or a vulnerability is exploited.
“As cloud service adoption accelerates and attack surfaces grow, enterprises need to move beyond siloed vulnerability management to secure their cloud environments. This is especially critical with customers maintaining multiple AWS accounts,” said Chris Labac, Vice President and General Manager, Network Performance and Threat Solutions, VIAVI. “The powerful combination of Observer Sentry with VIAVI’s industry-leading flow analysis takes threat exposure management to the next level by providing critical traffic visibility, enabling enterprises to identify, prioritize and remediate threats effectively.”
Observer Sentry is part of the VIAVI Network Performance and Threat Solutions (NPTS) portfolio. Enterprises worldwide leverage the Observer platform and its patented End-User Experience Scoring to continuously monitor and analyze end-to-end network and service architectures to ensure security and peak performance.