Sophisticated chips, sensors, and actuators in cars, industrial robots, or programmable logic controllers (PLCs) transmit data to the Industrial Internet of Things (IIoT) network. Distributed computing resources can use this data to convert insights into action, impacting business processes, and new ways of working. Various technical and security concerns remain unaddressed, but that’s changing.
Security is a significant concern with IoT that has slowed its deployment in critical application areas. Various IoT devices demonstrate security vulnerabilities. They become an easy target for DDoS attacks (Distributed Denial of Service). In this scenario, several compromised computer systems bombard a target–such as a central server–with a vast volume of simultaneous data requests. Following that, legitimate users are denied access to the service.
Another issue is that of scalability. As the number of devices connected through an IoT network grows, current centralized systems to authenticate, authorize, and connect different nodes in a network will turn into a bottleneck. To fix this, huge investments were necessary to deploy servers that can handle the information exchange, and the entire network can go down if the server becomes unavailable.
Another breakthrough technology could potentially address some of the IoT security and scalability challenges: blockchain, which is deemed to be an information game-changer. At its core, a blockchain system consists of a distributed digital ledger, shared between participants in the system, that resides on the internet. Transactions or events are validated and recorded in the ledger and cannot subsequently be amended or removed. It provides a way for information to be registered and shared by a community of users. Within this community, selected members maintain their copy of the ledger and must validate any new transactions collectively through a consensus process before they are accepted on to the ledger.
Built-in Security
A blockchain is a decentralized and distributed digital ledger used to record transactions across many computers so that any record involved can’t (easily) be altered retroactively without altering all subsequent blocks. This allows the participants to verify and audit transactions independently. A blockchain database is managed autonomously using a peer-to-peer network and a distributed timestamping server. Depending on the use case, people or machines and devices can trigger blockchain transactions. Typically, all participants can access and verify all data, including the full history of a blockchain. In many applications, this eliminates the need for a central trusted authority and trust between the participants. Authentication takes place by mass collaboration that’s in turn powered by collective self-interests. In terms of cryptocurrency, a blockchain confirms that each unit of value is transferred only once, solving double spending.
A blockchain network can be built several ways. They can be public, private, permissioned, or implemented by a consortium.
- A public blockchain is one that anyone can join and participate in, such as Bitcoin. Drawbacks might include substantial computational power required, little or no privacy for transactions, and weak security. These are essential considerations for enterprise use cases of Blockchain.
- A private blockchain network is a decentralized peer-to-peer network, with the significant difference that it’s governed by one organization. That organization controls who is allowed to participate in the network, execute a consensus protocol, and maintain the shared ledger. Depending on the use case, this can significantly boost trust and confidence between participants. A private blockchain can be run behind a corporate firewall and even be hosted on-premises.
- Businesses who set up a private blockchain will generally set up a permissioned blockchain network. It is important to note that public blockchain networks can also be permissioned. This places restrictions on who is allowed to participate in the network, and only in certain transactions. Participants need to obtain an invitation or permission to join.
- Multiple organizations can share the responsibilities of maintaining a blockchain. These pre-selected organizations determine who can submit transactions or access the data. A consortium blockchain is ideal for business when all participants need to be permissioned and have a shared responsibility for the blockchain.
Securing a Network
Blockchain can enable the fast processing of transactions and coordination among billions of connected devices. As the number of interconnected devices grows, the distributed ledger technology provides a viable solution to support a large number of transactions.
As the distributed ledger in a blockchain system is tamper-proof, trust verification is not needed for the most part among the involved parties. Going beyond the authentication issue, blockchain can also store IoT data. This adds another layer of security that hackers would need to bypass if they want to access the network. Blockchain provides a much more robust encryption level that makes it virtually impossible to overwrite existing data records.
Should the network be compromised, blockchain’s built-in transparency provides a reliable way to identify a specific source of data leakages and take remedial action. Anyone who is authorized to access the network can track the transactions that happened in the past.
A few organizations are dedicated to IoT and blockchain. The most famous is IOTA, a protocol for fast transaction settlement and data integrity, with a Tangle ledger that eliminates the need for expensive mining (validation of transactions). IOTA is a promising infrastructure for IoT devices that need to process large amounts of microdata. Features of the Tangle ledger, the distributed ledger that supports IOTA, are machine-to-machine communication, fee-less micropayments, and quantum-resistant data.
Another player is Chain of Things (CoT), a consortium of technologists and blockchain companies. It investigates the best possible use cases where a combination of blockchain and IoT can offer significant benefits to industrial, environmental, and humanitarian applications. So far, CoT has built Maru, an integrated blockchain and IoT hardware solution to solve issues with identity, security, and interoperability. Three developed use cases are available and named Chain of Security, Chain of Solar, and Chain of Shipping.
Riddle&Code provides cryptographic tagging solutions for blockchains in smart logistics and supply chain management. Working on the integration between IoT devices and distributed ledger networks, Riddle&Code offers a combined, patented hardware and software solution that enables secure and trusted interaction with machines in the IoT age–by giving physical devices a trusted digital identity. This technology breaks through the physical/digital divide to balance the demand for paper documentation and the advantages that blockchain technology offers.
Combining IoT sensors with blockchain technology, Modum.io provides data integrity for transactions involving physical products. Modum sensors record environmental conditions, such as temperature, that goods are subject to while in transit. When the goods arrive at the next transit point or end customer, the sensor data is verified against predetermined conditions in a smart contract on the blockchain. The contract validates that the terms meet all of the requirements set out by the sender, their clients, or a regulator and triggers various actions such as notifications to sender and receiver, payment, or release of goods.
Hardware security
The typical entry point for malicious entities is the same as that for goodones: Access credentials are generally regarded as the weakest areas.
The success of a blockchain system hinges on secured user access to the distributed database. If an attacker gains access to another user’s highly confidential credentials, the attacker would have full control over that blockchain account (currency, assets, ID, contracts, etc.). Similarly, if users lose their credentials, they lose access to all blockchain assets and can no longer use or valorize them. Additionally, transactions and operations stored in a blockchain cannot be simply undone. Hardware-based security tokens are one effective way against attacks and unauthorized access.
Storing blockchain user credentials on a computer or a cellphone is extremely risky as an attacker might identify and read confidential information. This could even be done remotely utilizing software attacks. Integrating a dedicated Hardware Security Module (HSM) into the device microcontroller can significantly enhance security. This separates critical operations and credential storage from other software operations and therefore provides robust protection against software attacks.
A dedicated security controller allows achieving the highest possible security level for critical operations and credential storage. This security controller has additional countermeasures to protect against physical attacks. One example is Infineon’s Blockchain Security 2Go starter kit that provides a fast way (Figure 1) to build security into blockchain system designs.

The starter kit contains five NFC smart cards based on Infineon’s security controller with blockchain crypto features for several blockchains. Additionally, an open-source Android app for Ethereum and Smart contract examples is provided. The NFC smart cards help blockchain system designers to easily integrate hardware-based security (Figure 2) and quickly develop prototypes of the blockchain application.
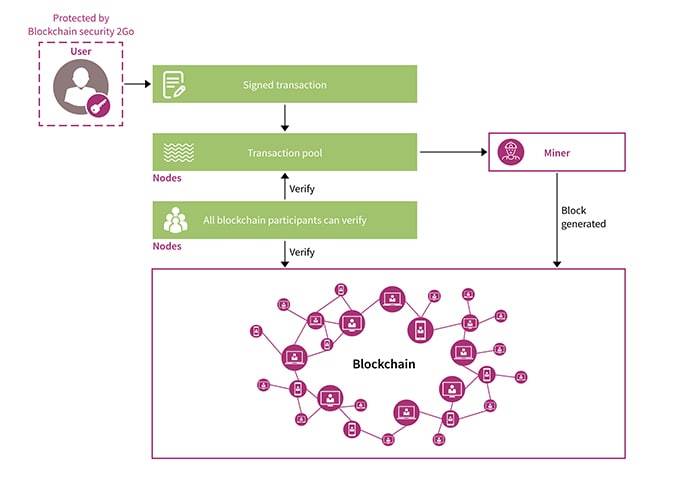
The security tokens–whether they’re smart cards, dongles, or solutions for mobile devices–allow users to generate their unique public and private key pairs securely, authenticate with a PIN and sign their data and digital transactions. All the user credentials can be stored in the security controller and be protected from remote attacks on software or the micro-architecture, especially from physical attacks if the token is stolen or lost.
About the Author

As Technical Content Specialist, Marcel is the internal contact person for technical questions in Mouser’s EMEA marketing team. Originally a physicist, he used to work as editor for special-interest magazines in electronics. In real life, he’s juggling two kids with too many chromosomes, a penchant for electronic gadgets and a fondness of books and beer. Until now, none has dropped.















