In the dynamic landscape of technological advancements, the rise of the Internet of Things (IoT) and Industrial IoT (IIoT) has ushered in a new era of connectivity and efficiency across industries. While these interconnected systems promise tremendous benefits, they also introduce a range of security challenges that require careful consideration and proactive solutions. This article dives deeper into the security challenges inherent in IoT and IIoT and offers comprehensive strategies to fortify these networks and protect sensitive data.
The Inadequate Testing and Upgradation Challenge
IoT devices have become an integral part of modern life, offering convenience, efficiency, and connectivity. These devices, ranging from smart thermostats and wearable devices to industrial sensors and medical equipment, communicate with each other and the internet, enabling them to collect and exchange data. Manufacturers of IoT devices are often under pressure to bring new and innovative products to market quickly. This pressure to innovate and the desire for a competitive edge can lead to a rush in product development, potentially sidelining thorough security testing. The consequences of inadequate security in IoT devices can be severe. Breaches in security can compromise user privacy, lead to financial losses, and even endanger physical safety in cases where IoT devices control critical systems like industrial machinery or medical equipment.
To address the challenges posed by inadequate security testing and the potential vulnerabilities it introduces, there are several key steps that manufacturers, developers, and users can take:
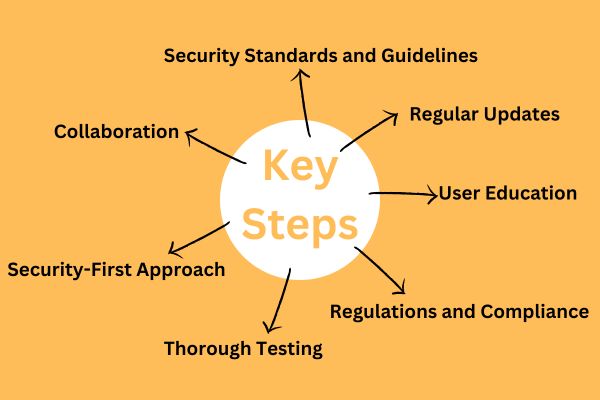
Network Problems as a Security Hurdle
While flat networking is integral to IoT efficiency, it can also be a conduit for security breaches. To mitigate this challenge, effective network segmentation combined with robust access controls is essential. Industrial IoT solution providers should place network configuration at the forefront of their strategies, preventing unauthorized access and safeguarding against potential breaches.
Adequate Consolidation of Data
The sheer volume of data generated by IoT devices necessitates meticulous data consolidation strategies. Implementing secure data storage, robust transmission protocols, and stringent access controls are paramount. Employing advanced encryption and authentication mechanisms ensures that sensitive data remains shielded from unauthorized access, preserving its confidentiality and integrity.
Data Encryption: Converting Data into Code
The significance of data encryption cannot be overstated. Data encryption acts as a formidable barrier against cyber threats by rendering intercepted data unreadable and unusable. Without encryption, IoT-generated data becomes susceptible to interception and manipulation. Utilizing state-of-the-art encryption protocols guarantees the safe transmission and storage of data, thwarting potential cyber-attacks.
Hardware Security
At the heart of IoT security lies hardware integrity. The onus falls on chip manufacturers to embed robust security features directly into the hardware. This includes secure boot processes to ensure device integrity from startup, tamper-resistant components that resist unauthorized access, and hardware-based encryption that adds an extra layer of data protection.
The Imperative of Security in IIoT
The unique integration of Industrial IoT into critical infrastructure demands an elevated level of security consciousness. Breaches in IIoT systems can have dire consequences, including severe business disruptions and potential loss of life. To counteract these risks, a comprehensive security strategy encompassing risk assessment, regular maintenance, and stringent security protocols is pivotal for safeguarding IIoT deployments.
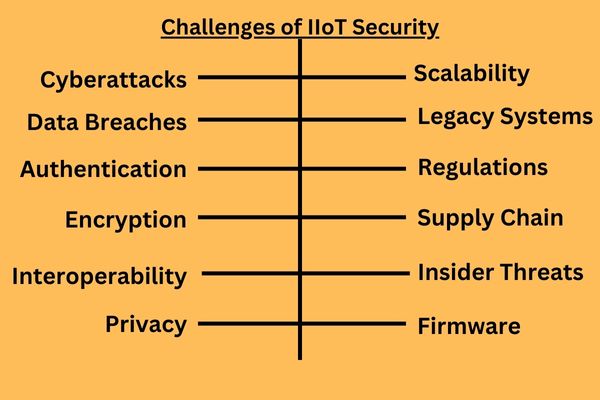
Challenges of IIoT Security
In the realm of Industrial IoT, specific challenges emerge, including the inadequate maintenance of legacy software and the lack of standardized security protocols. These issues can be mitigated through adherence to strict software development lifecycles, the integration of risk assessment modules, implementation of hardware integrity measures, and robust encryption protocols.
Effective Strategies for Safeguarding Connected Systems
- Collaborative Self-Regulation: The IoT and IIoT industry should unite to develop standardized security protocols and practices. This collective effort establishes a minimum security baseline for all devices, creating a more resilient ecosystem.
- Segmented Network Architecture: The segregation of IT networks isolates critical industrial control systems from general infrastructure, minimizing the attack surface and bolstering security.
- Robust Endpoint Protection: Implementing reliable endpoint protection mechanisms prevents unauthorized access and unauthorized changes to IoT and IIoT devices, maintaining the integrity of these systems.
- Strong Encryption: Encryption remains the cornerstone of data protection. Employing robust encryption algorithms safeguards data during transmission and storage, ensuring its confidentiality and resilience against attacks.
- Regular Maintenance and Updates: Consistent updates and patches are pivotal to addressing vulnerabilities and enhancing security. Regular maintenance ensures that IoT and IIoT devices remain resilient to evolving threats.
Conclusion
As the realms of IoT and IIoT continue to expand, the importance of addressing security challenges becomes increasingly urgent. Collaboration among IoT device manufacturers, service providers, and industrial organizations is paramount to prioritize security from the outset. Through rigorous testing, hardware security measures, standardized protocols, and encryption strategies, the IoT and IIoT industry can forge a path toward a secure and prosperous interconnected future. The journey toward safeguarding connected systems may be complex, but the dividends in terms of enhanced safety, efficiency, and innovation make the endeavor more than worthwhile. By remaining vigilant and proactive, the industry can pave the way for a resilient digital landscape that safeguards both data and lives.















